Many of the leading cyber security teams use Feedly to organize and automate their open-source threat intelligence and stay ahead of emerging threats. We have had the chance to research 100 of them and review their open-source threat intelligence best practices.
In this article, we will share how they translate their intelligence needs into various types of feeds and how they structure those feeds into a highly functional Feedly account.
Track trending cybersecurity news
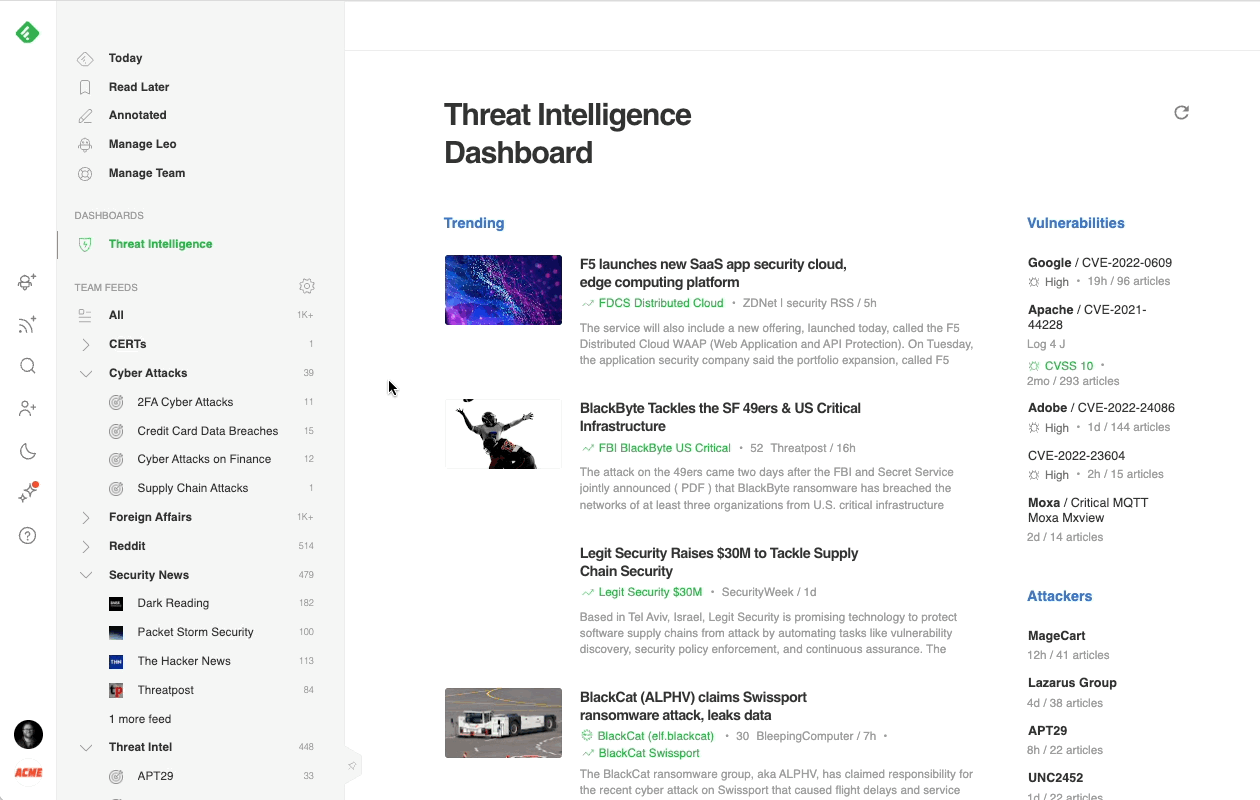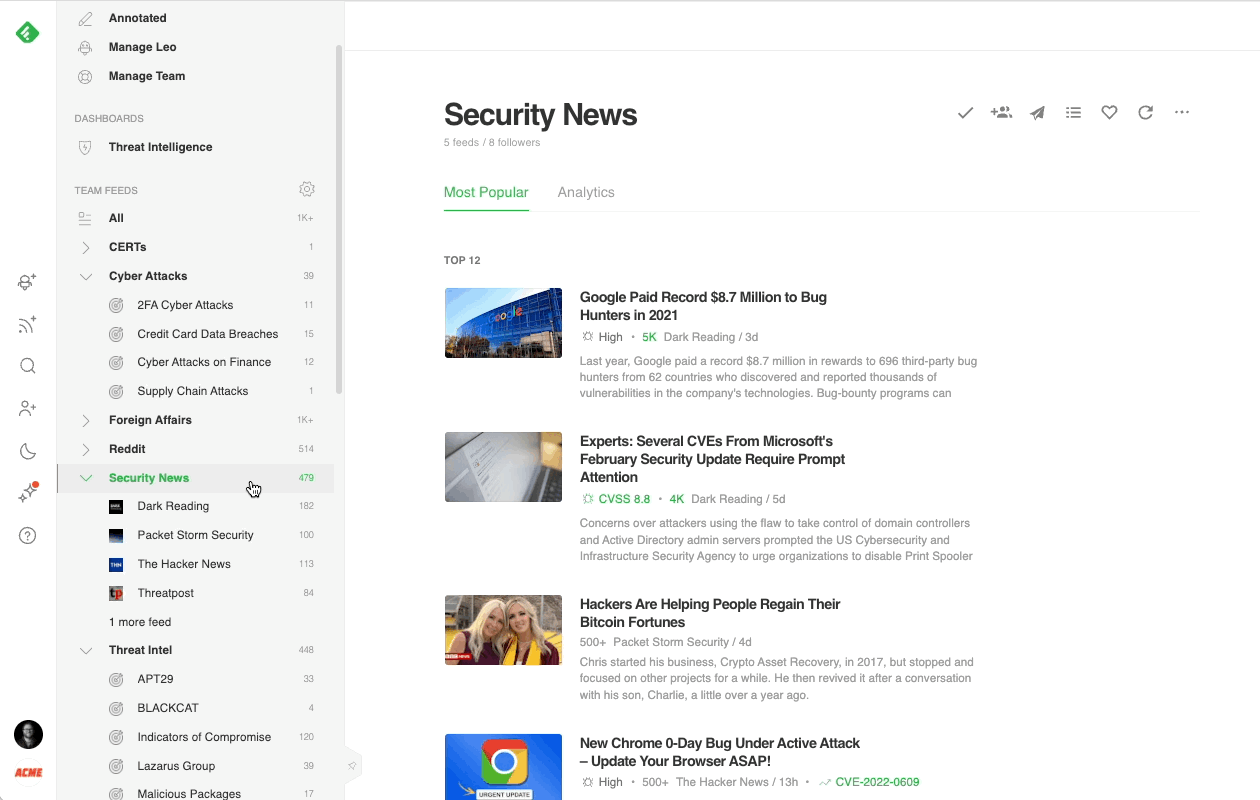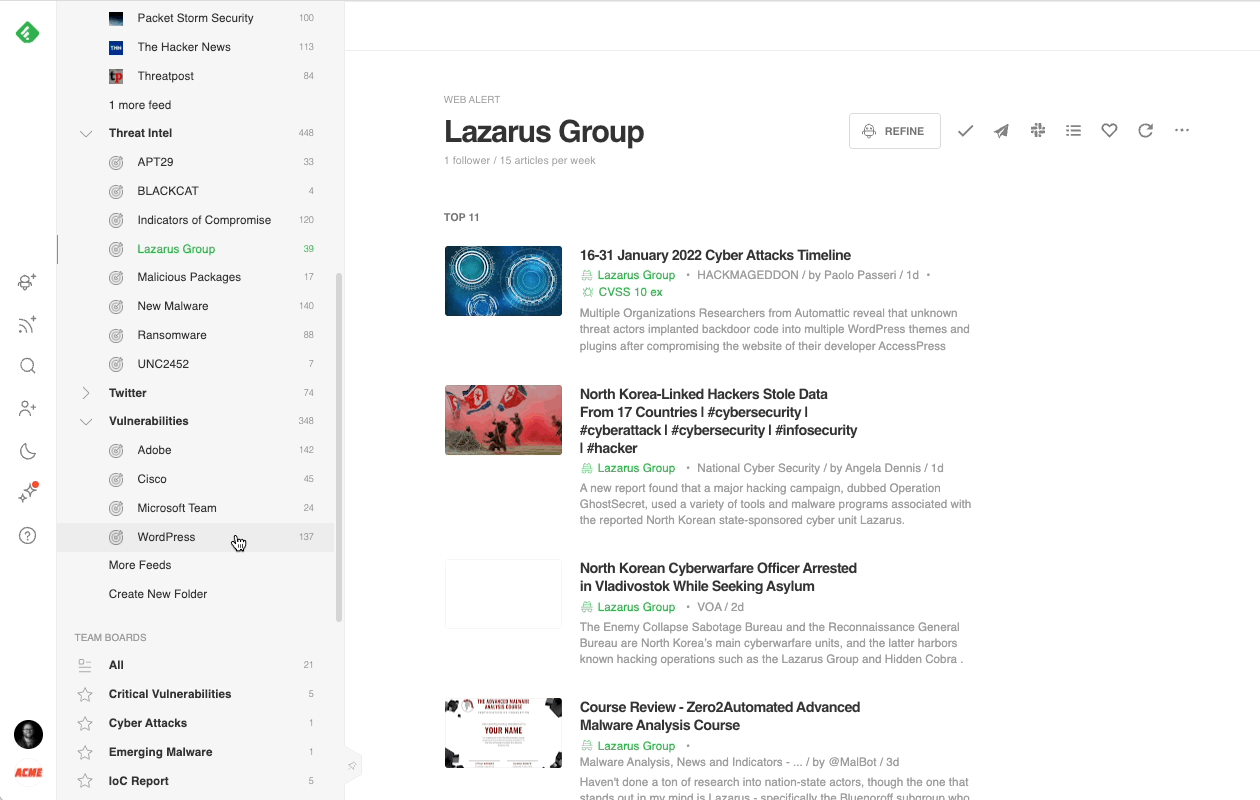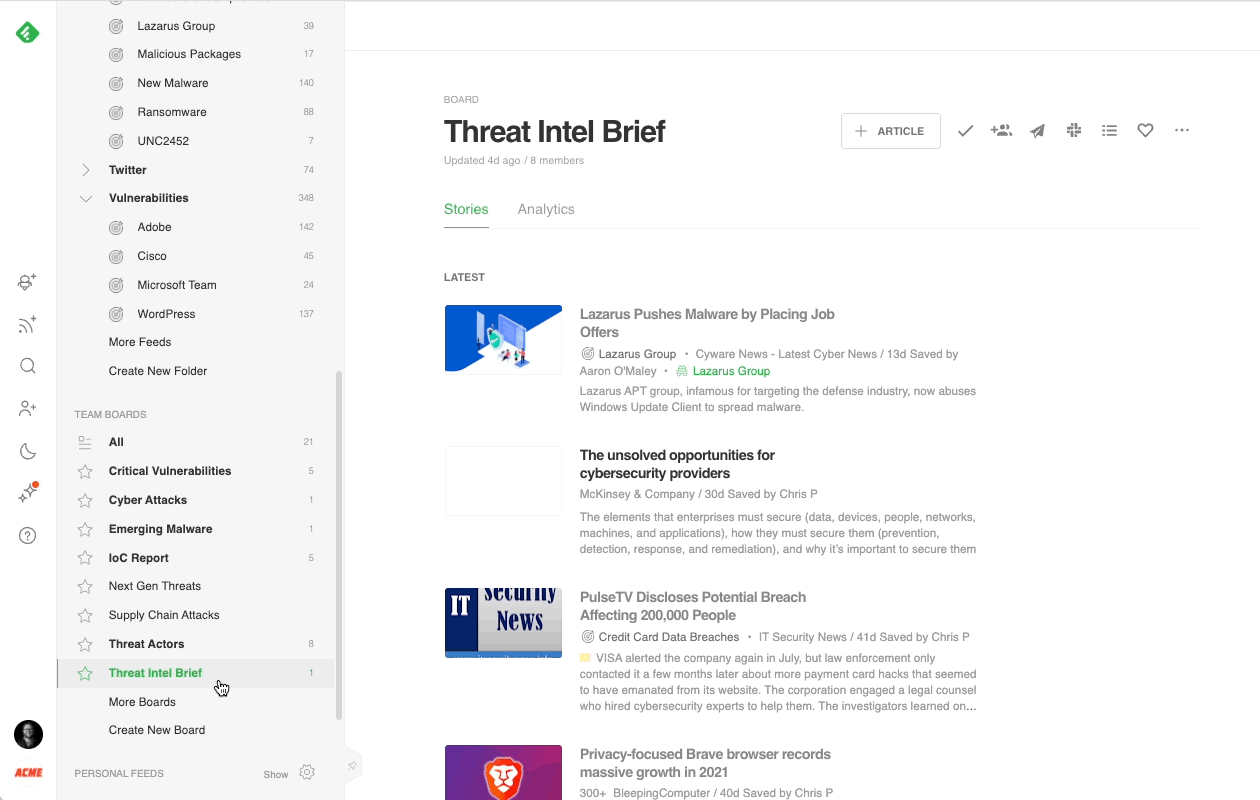
Most cybersecurity professionals start their day in the Threat Intelligence Dashboard. It offers a broad overview of the emerging threat landscape: trending cybersecurity articles and attacks, new critical vulnerabilities, active attackers, new behaviors, and malware families, so it’s easy to get a sense of what’s going on in just a few minutes.
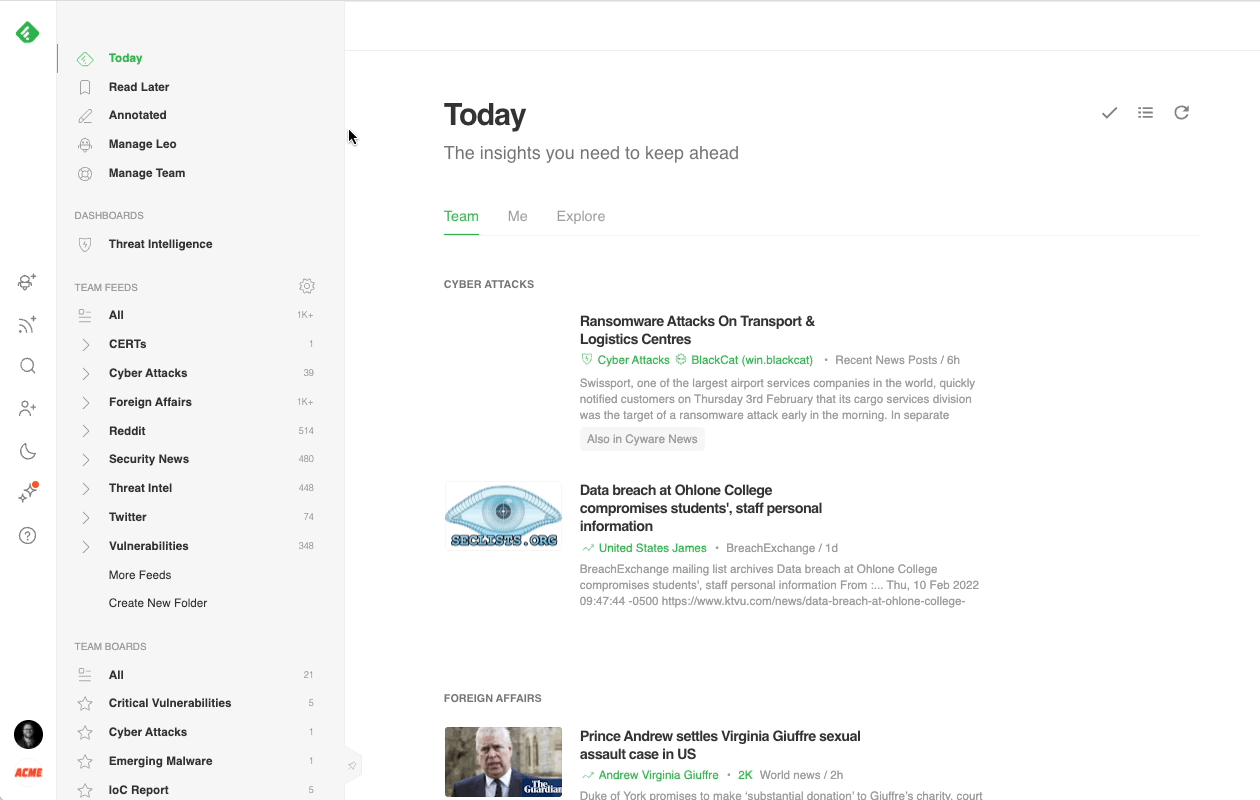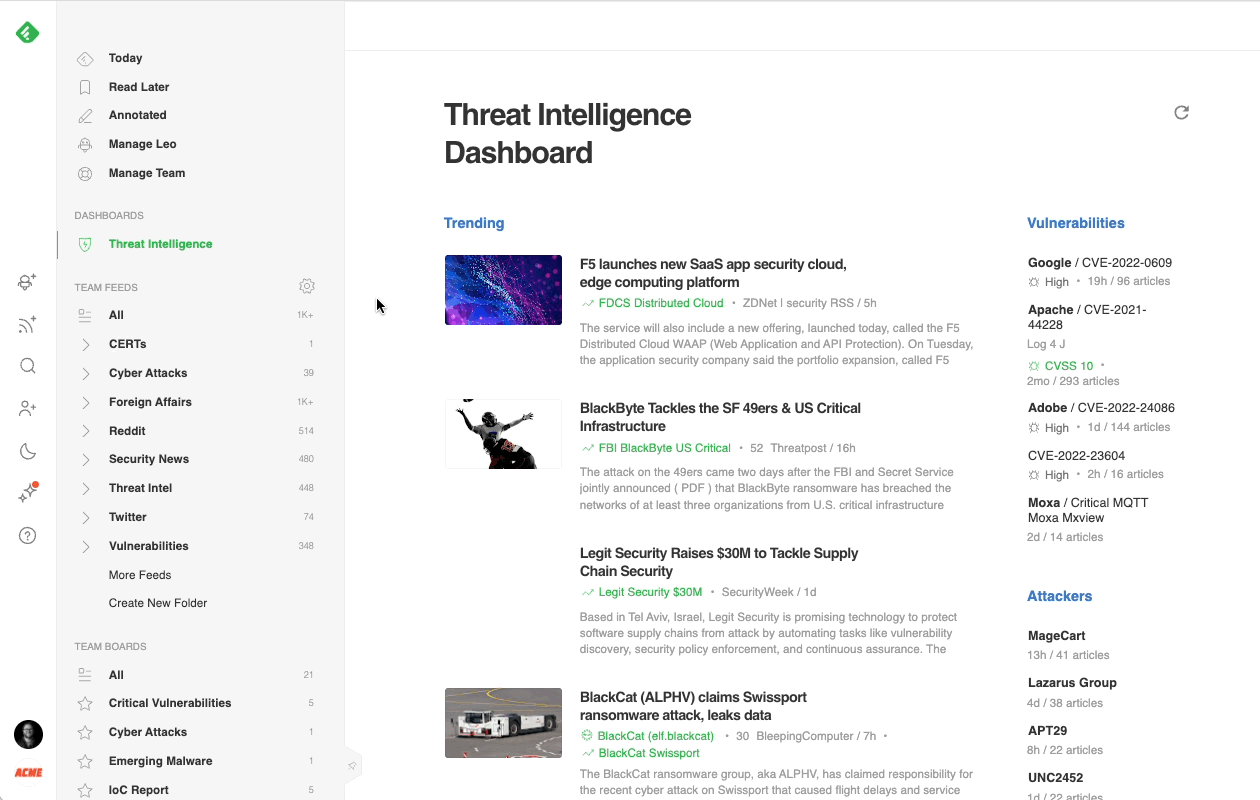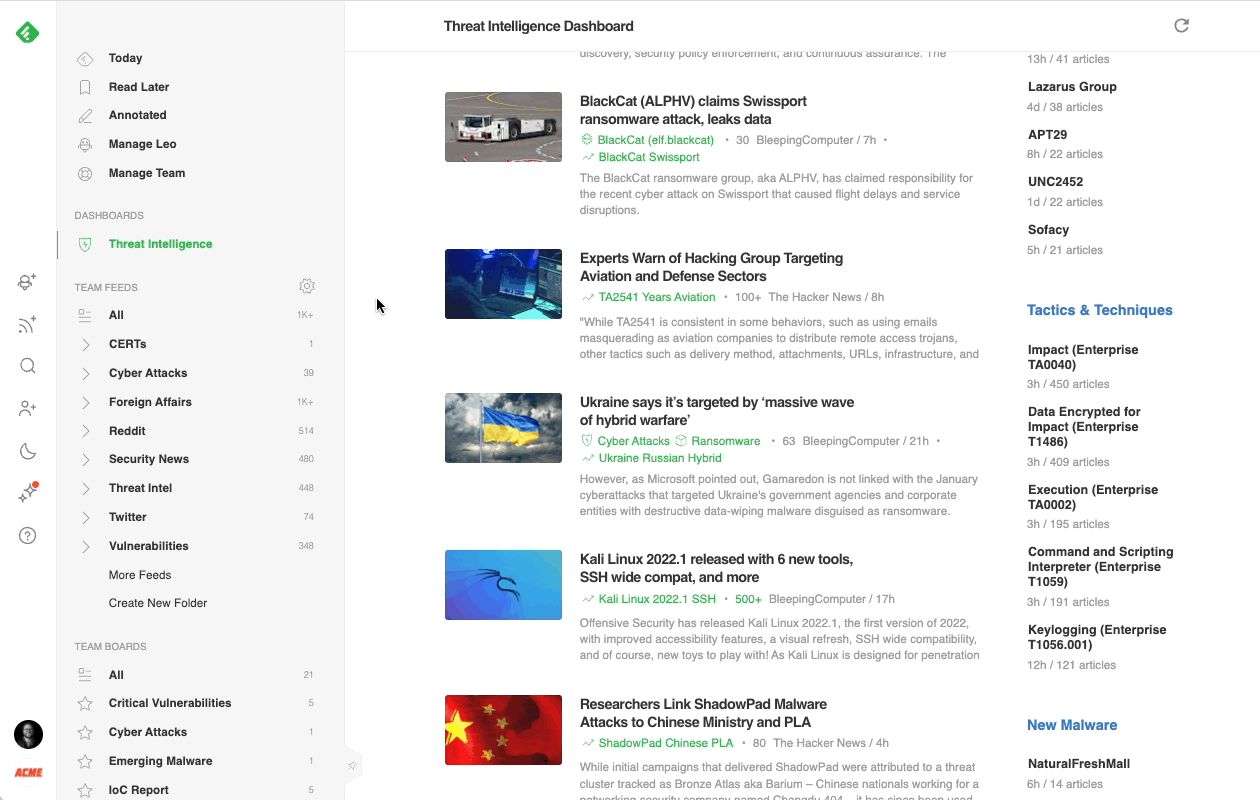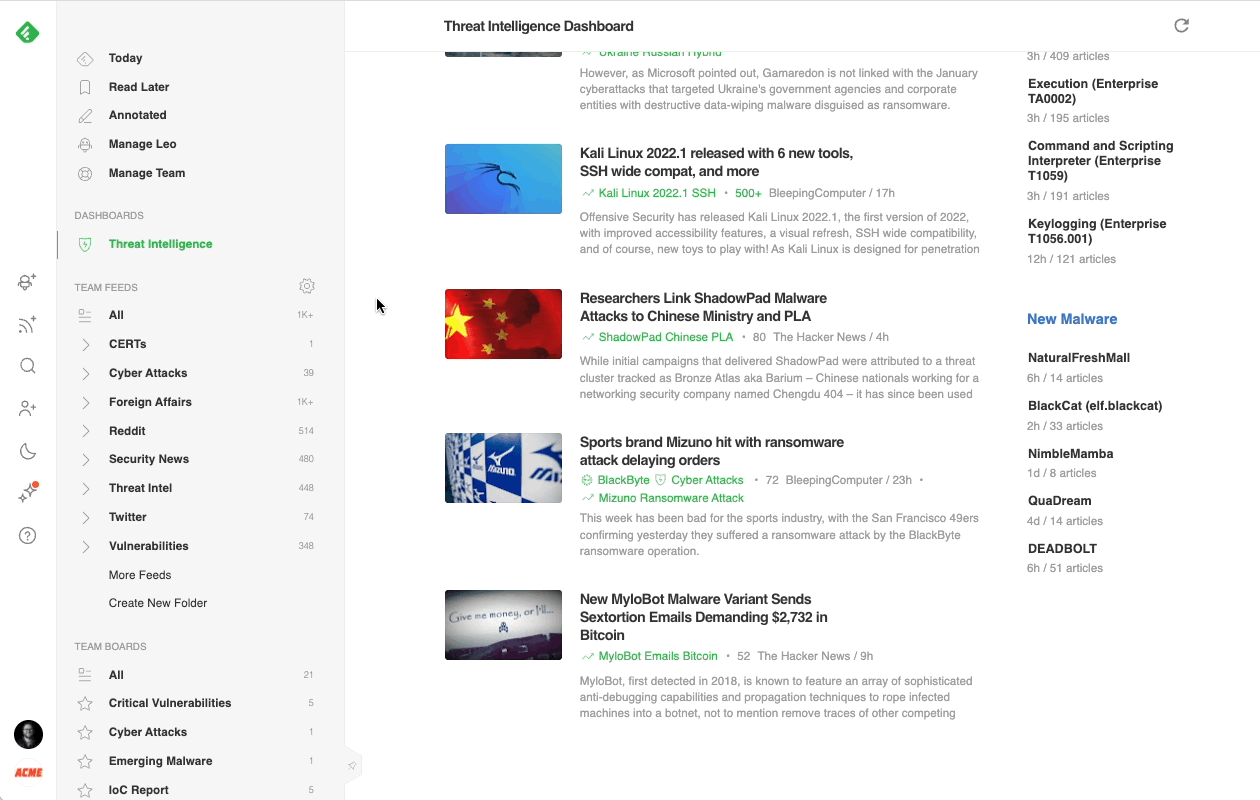
Here’s a brief overview of each section:
- Trending News: Stay ahead of attacks by seeing which threats are trending in the cybersecurity community.
- Vulnerabilities: Improve reaction time and respond quickly to new vulnerabilities as they arise, allowing cybersecurity teams and their clients to stay informed of oncoming risks faster.
- Attackers: Identify at a glance which Threat Actors are trending and quickly create Web Alerts to track their actions and behaviors.
- Tactics & Techniques: Keep track of which TTPs are proving to be the most prevalent among Threat Actors, map data to the Mitre ATT&CK Navigator to compare with other Threat Actor Profiles, or to identify gaps in your defensive capability.
- New Malware: Research what New Malware is affecting systems and be vigilant against emerging threats.
Discover critical vulnerabilities
The most effective way to track critical vulnerabilities and zero-days across the web is with Feedly AI. Feedly AI has been pre-trained to understand vulnerabilities and assess their severity. It reads millions of articles every day, looking for critical security threats.
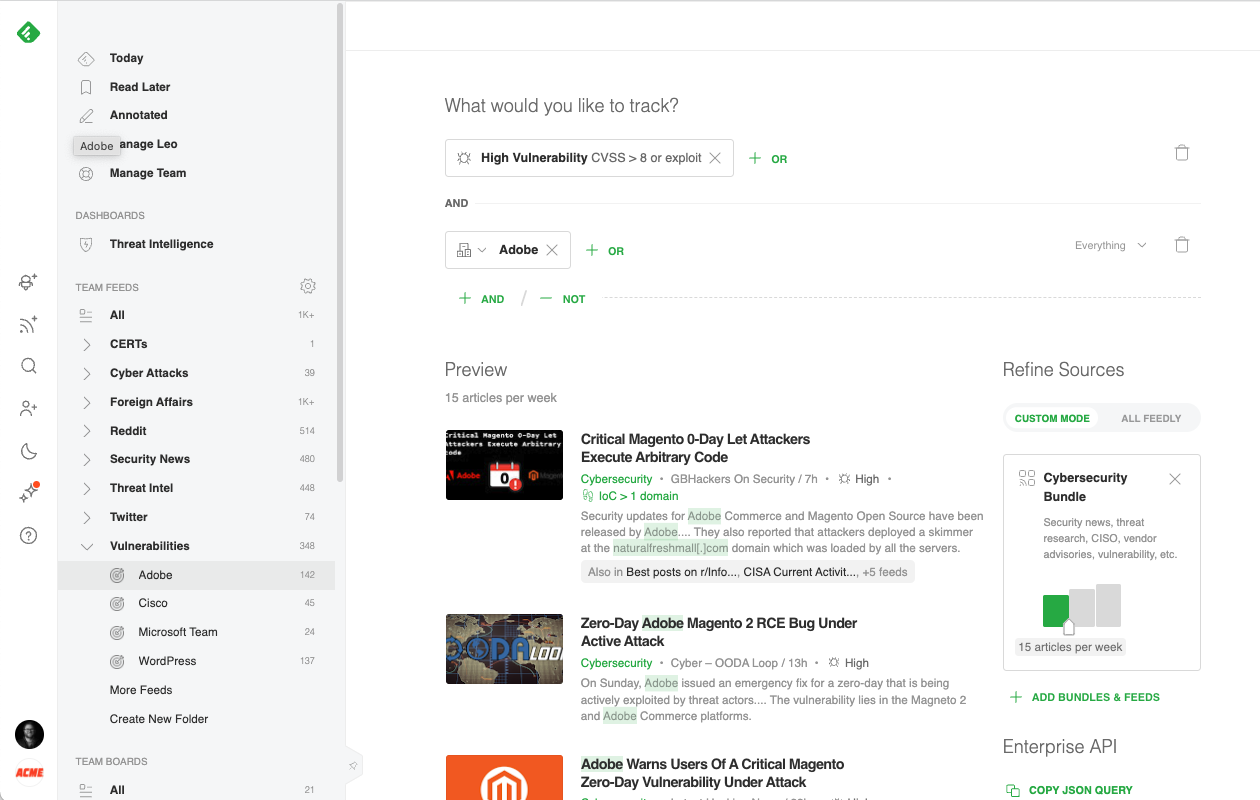
When Feedly AI finds a CVE, it automatically searches for its CVSS score, related exploits and malware families, links to threat actors, CWE information, and patches. It then organizes all this information into a rich CVE insights card.
If the CVE doesn’t have a CVSS score yet, Feedly AI uses machine learning to predict the CVSS score, keeping you one step ahead of the latest emerging threats.
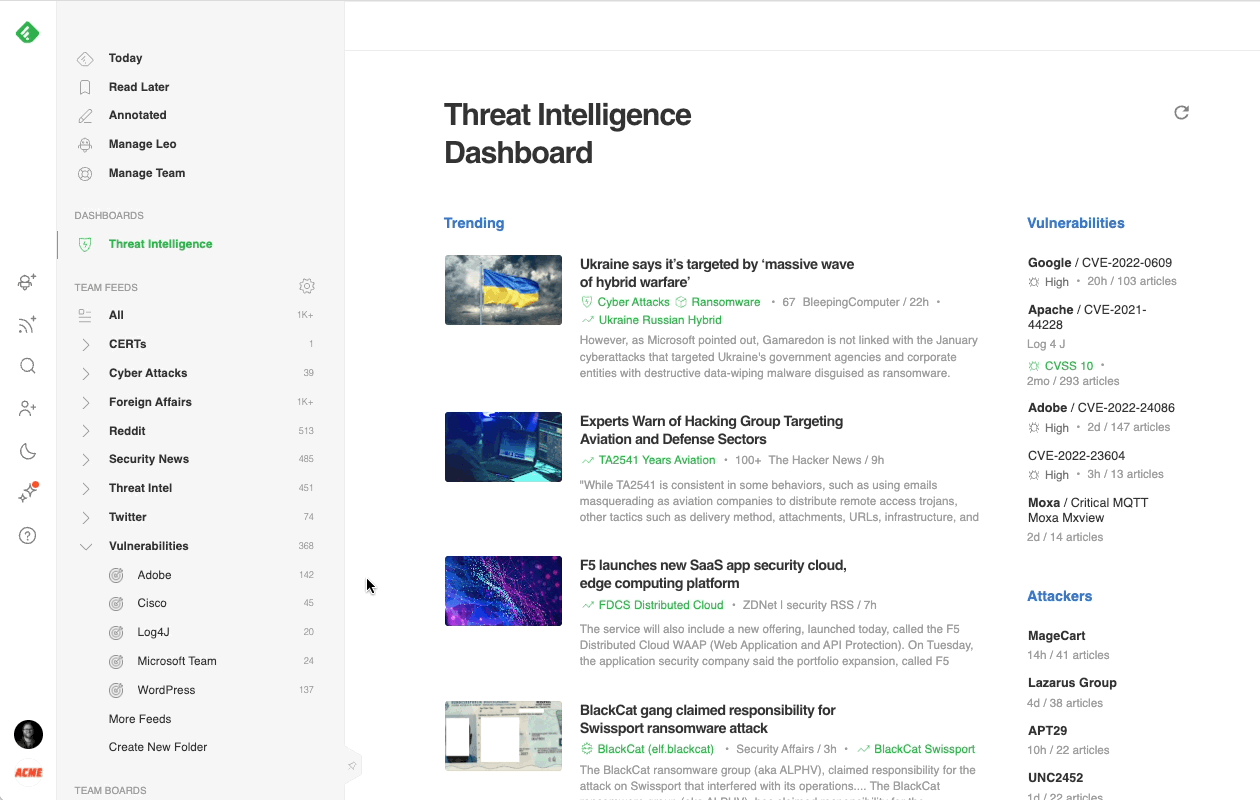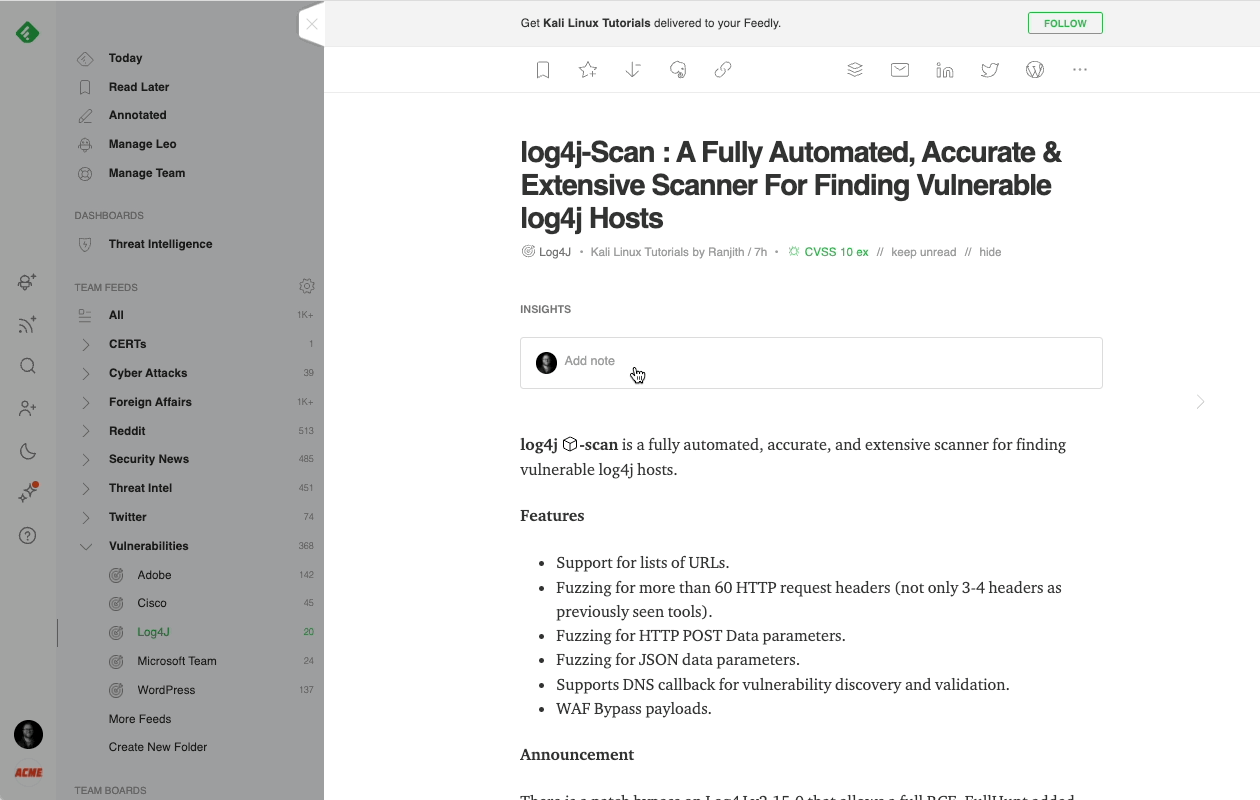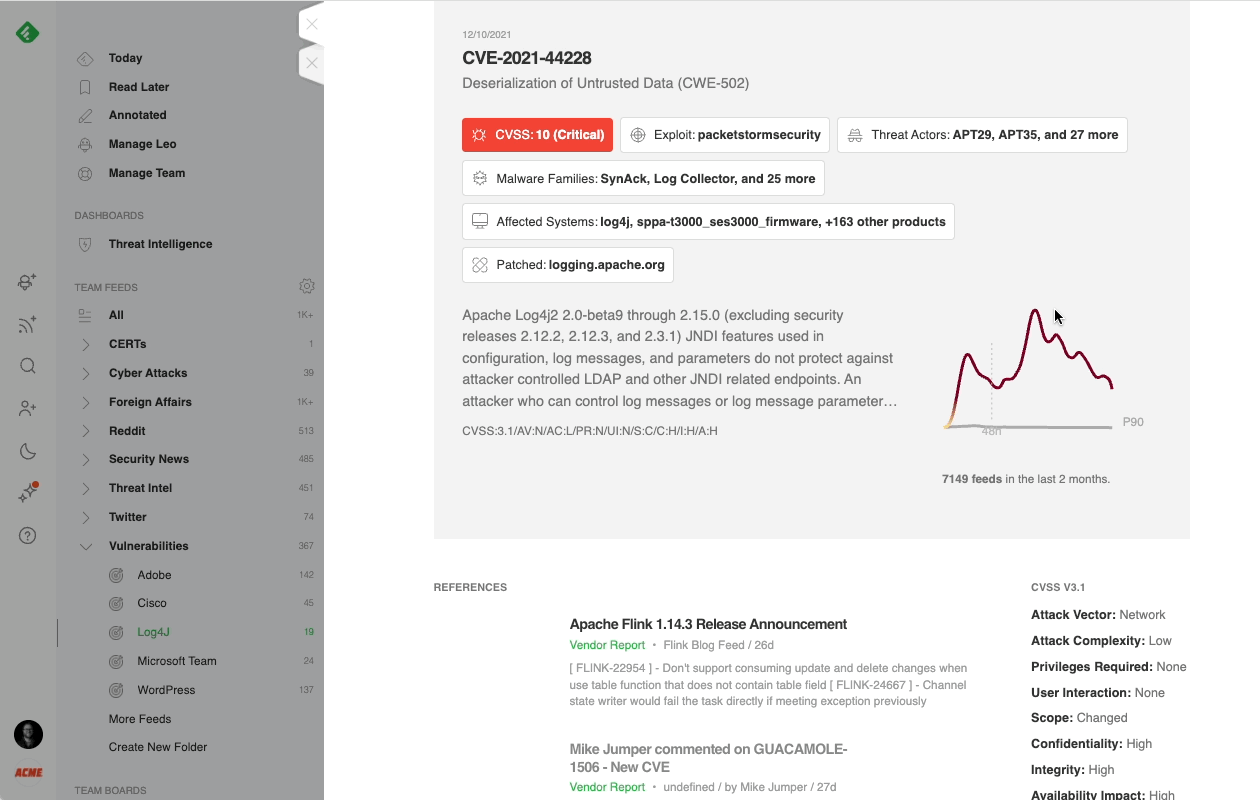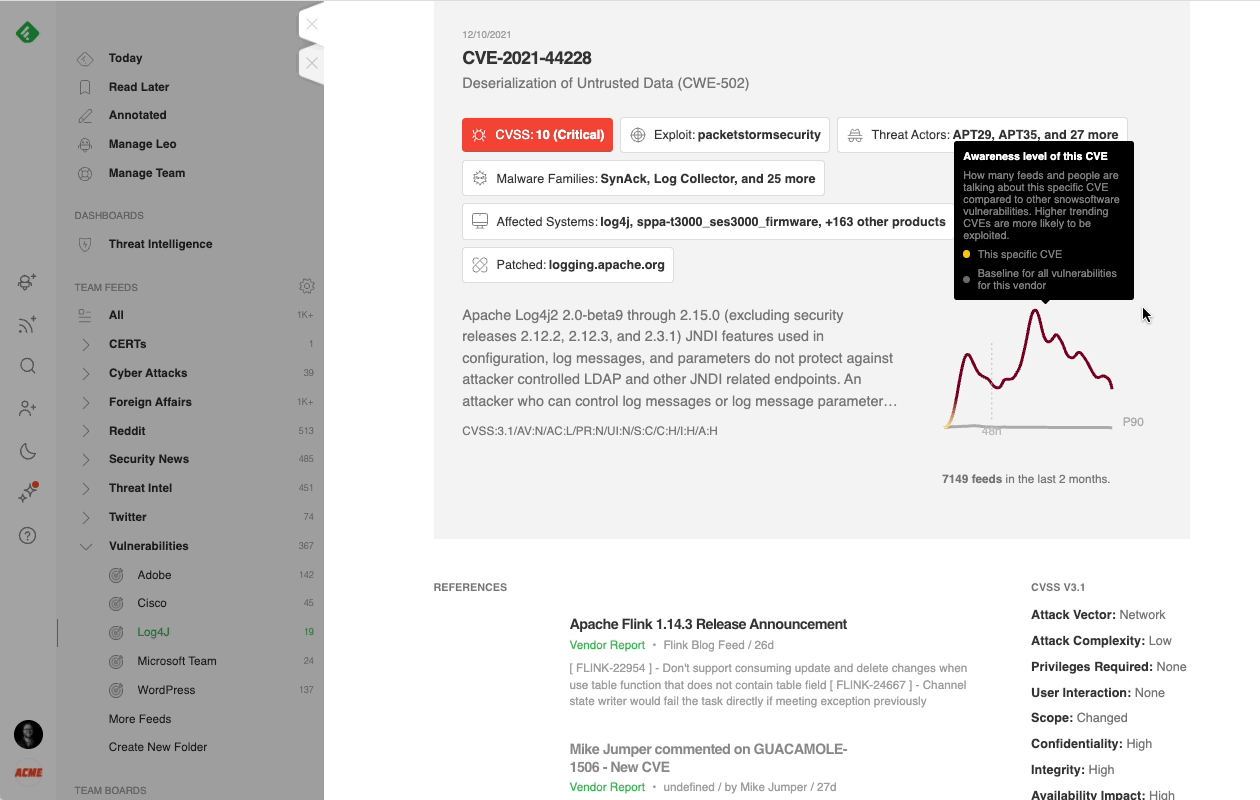
Creating a broad (Feedly) AI Feed targeting all critical vulnerabilities gives you a big picture view of what is happening across the threat landscape, while adding specific vendors to the search narrows the focus into more precise and manageable feeds.
Cybersecurity teams often create an AI Feed for each of the main products deployed in their environment and group them into a Vulnerabilities folder.
Track adversary behaviors
One way cybersecurity teams track and visualize the behaviors of specific Threat Actors and Malware Families is by using Feedly’s integration with the Mitre ATT&CK framework. Feedly AI has been pre-trained to understand threat actors (integration with Malpedia), Mitre ATT&CK (version 10), and the model of threat intelligence reports. These three models can be easily combined to track the behavior of selected adversaries.
Here is an example of an AI Feed surfacing all the threat intelligence reports mentioning the Lazarus Group threat actor:
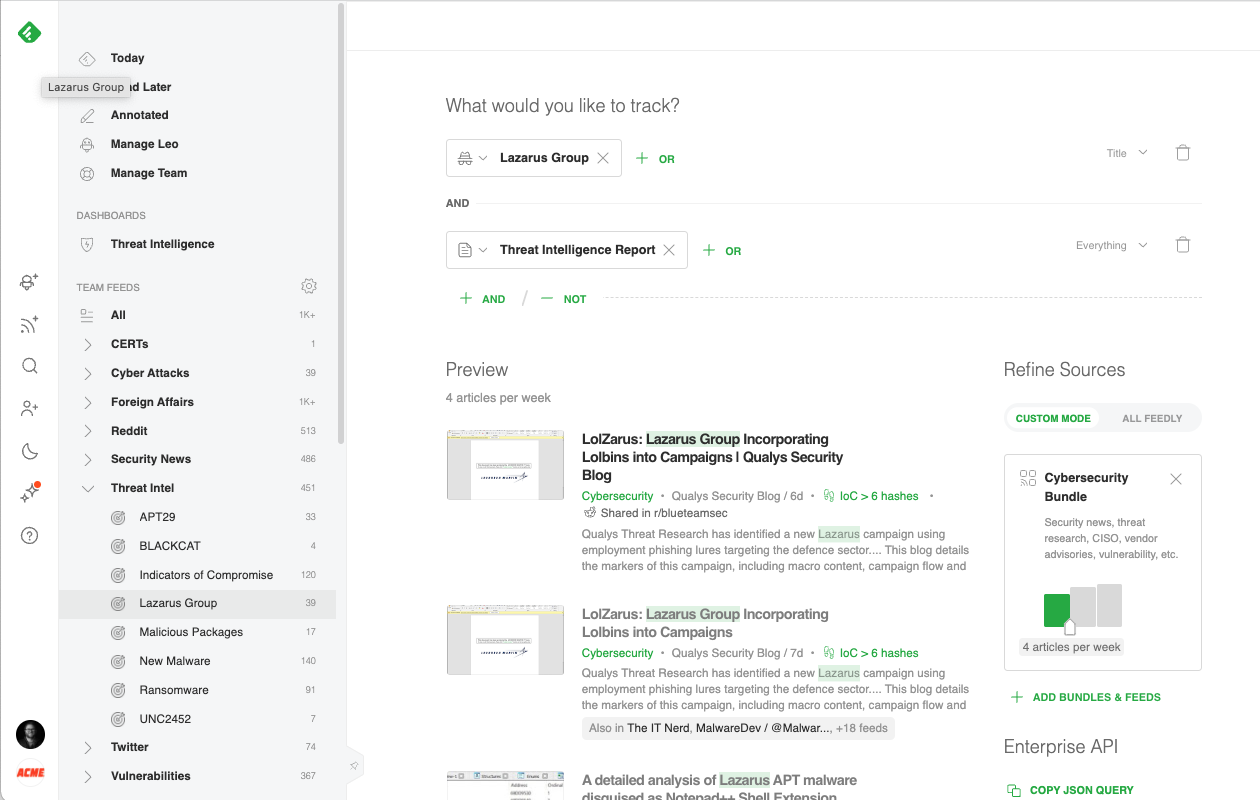
Cybersecurity teams often create an AI Feed for each of the threat actors and malware families defined on their threat profiling list and group them into a “Threat Intel” folder.
When Feedly AI finds an article in which it has identified TTPs, it can map the content of that article to the ATT&CK navigator so that cybersecurity teams can easily analyze the adversary behavior and compare it with their existing defenses.
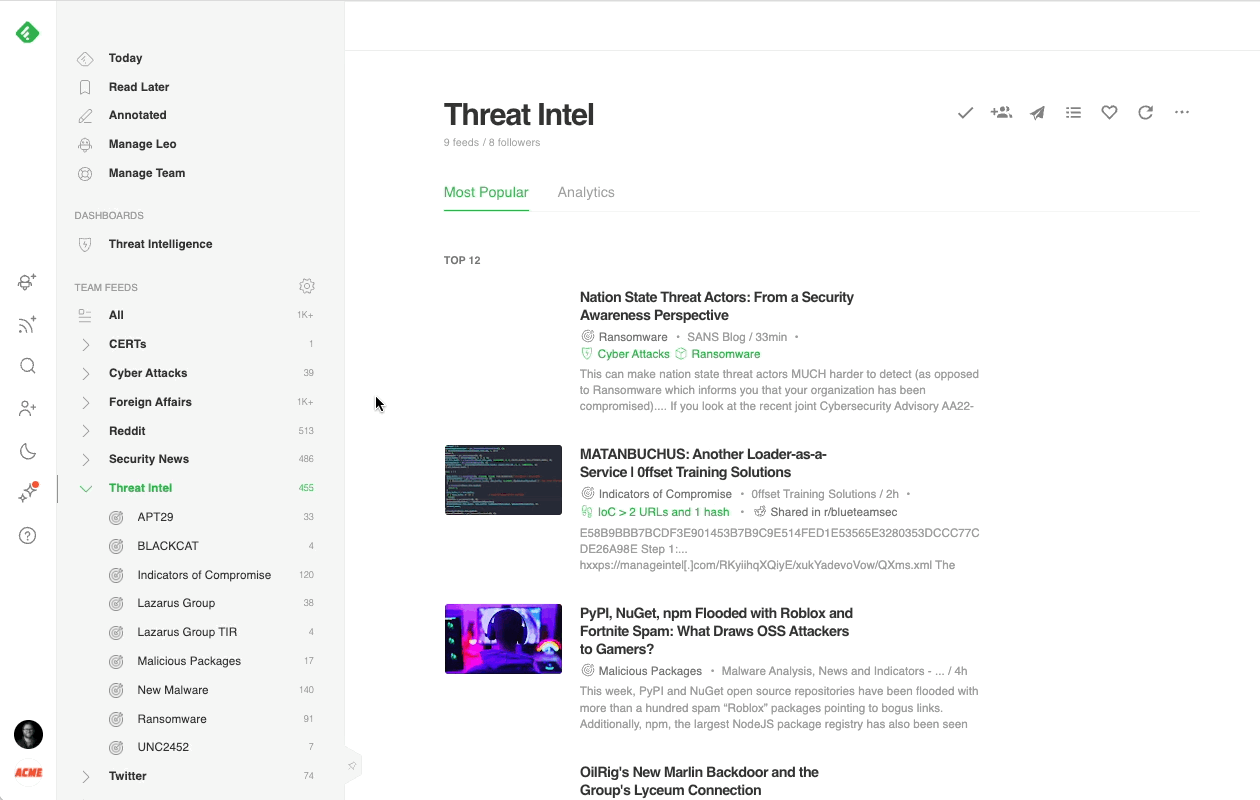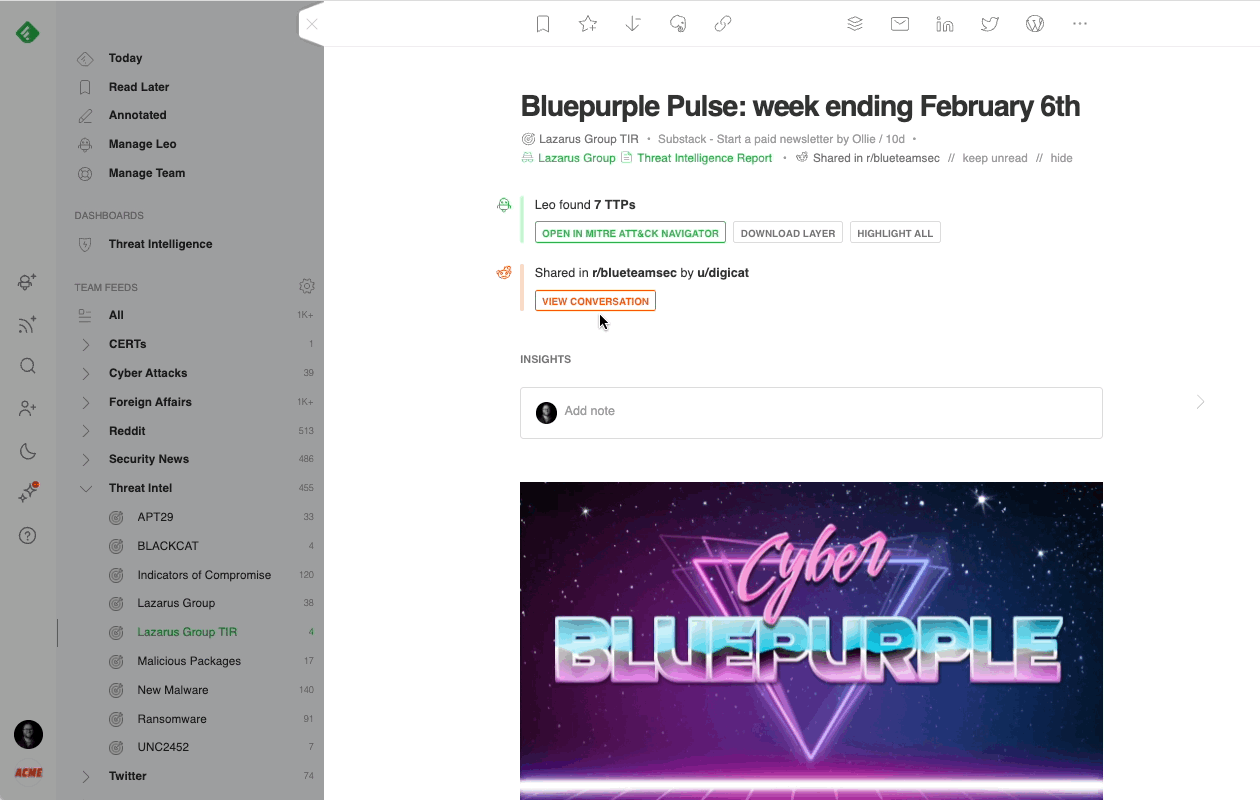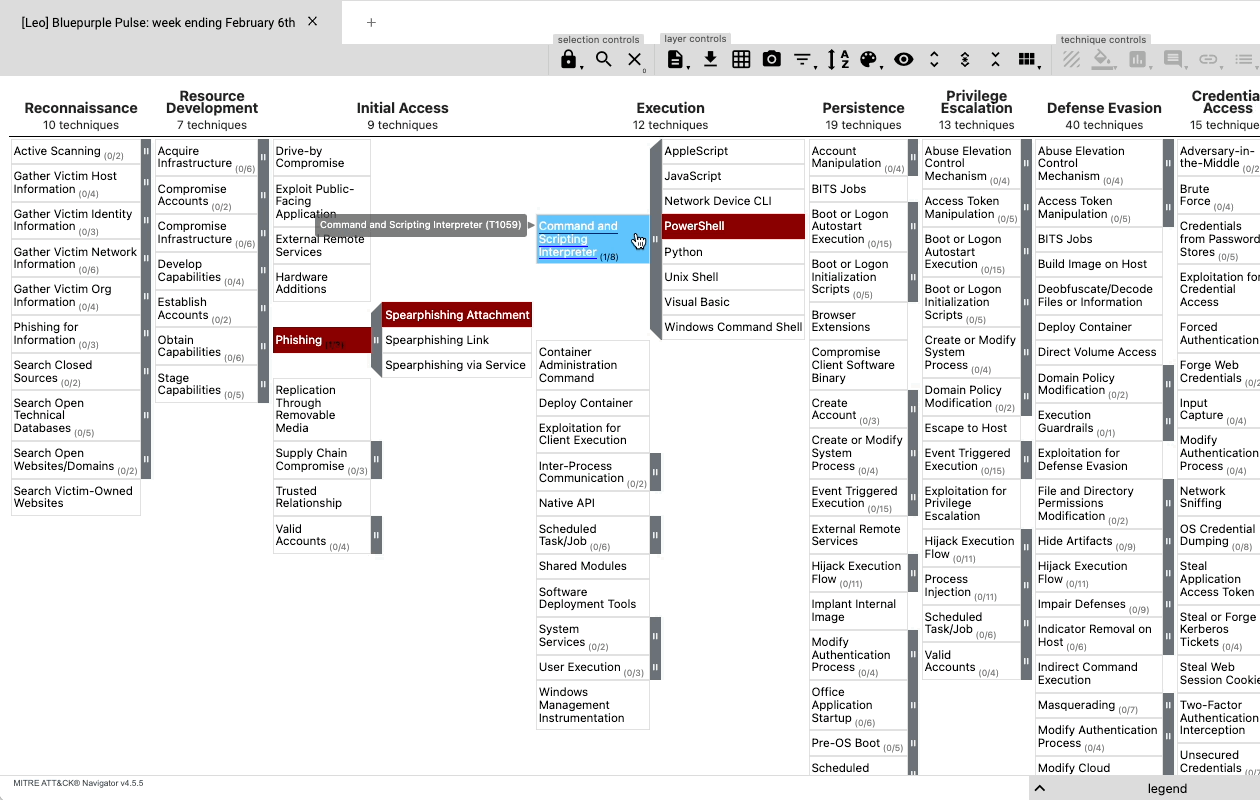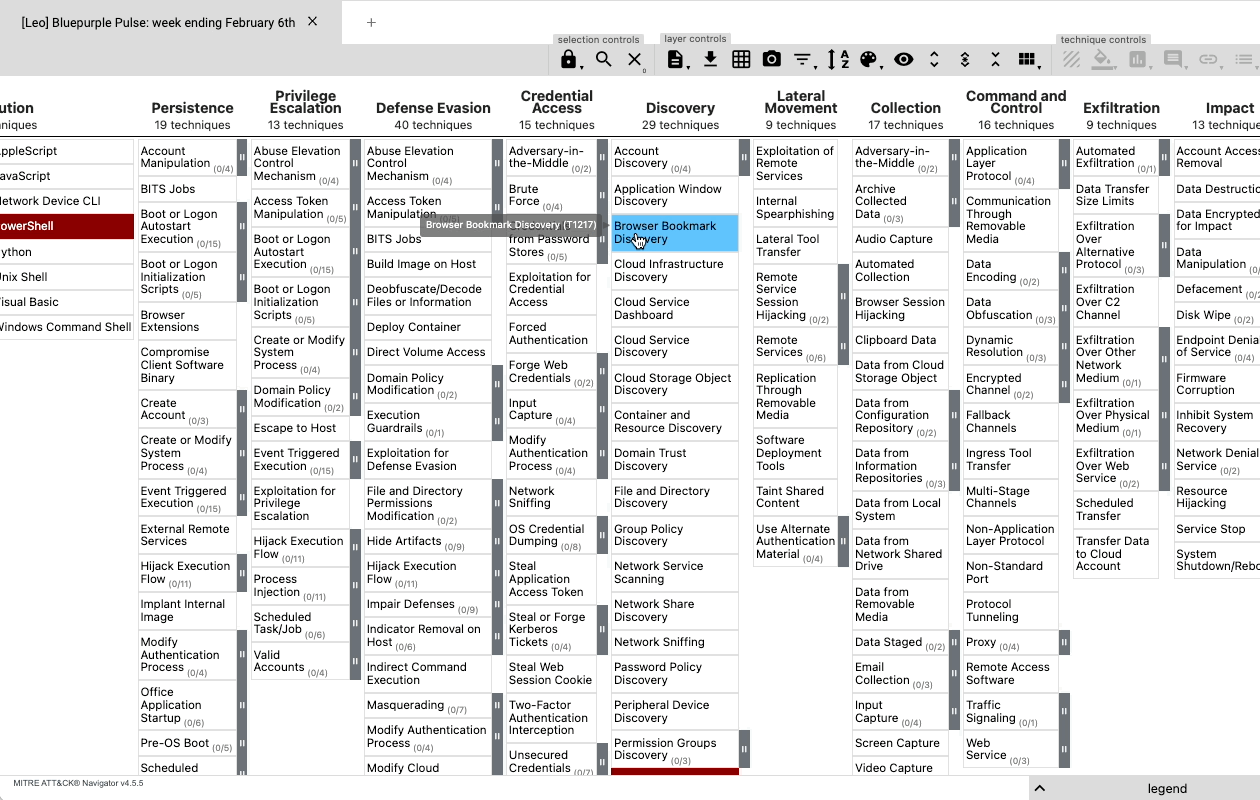
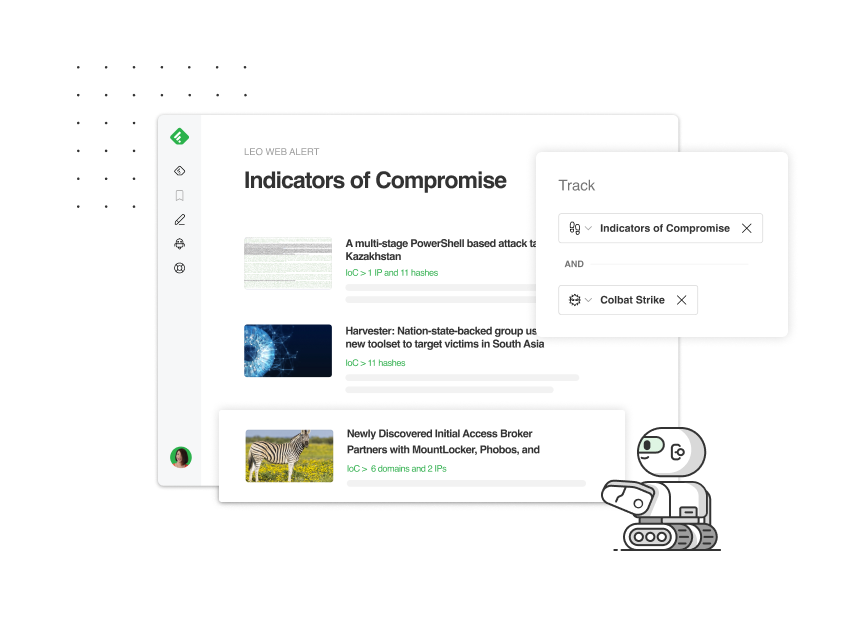
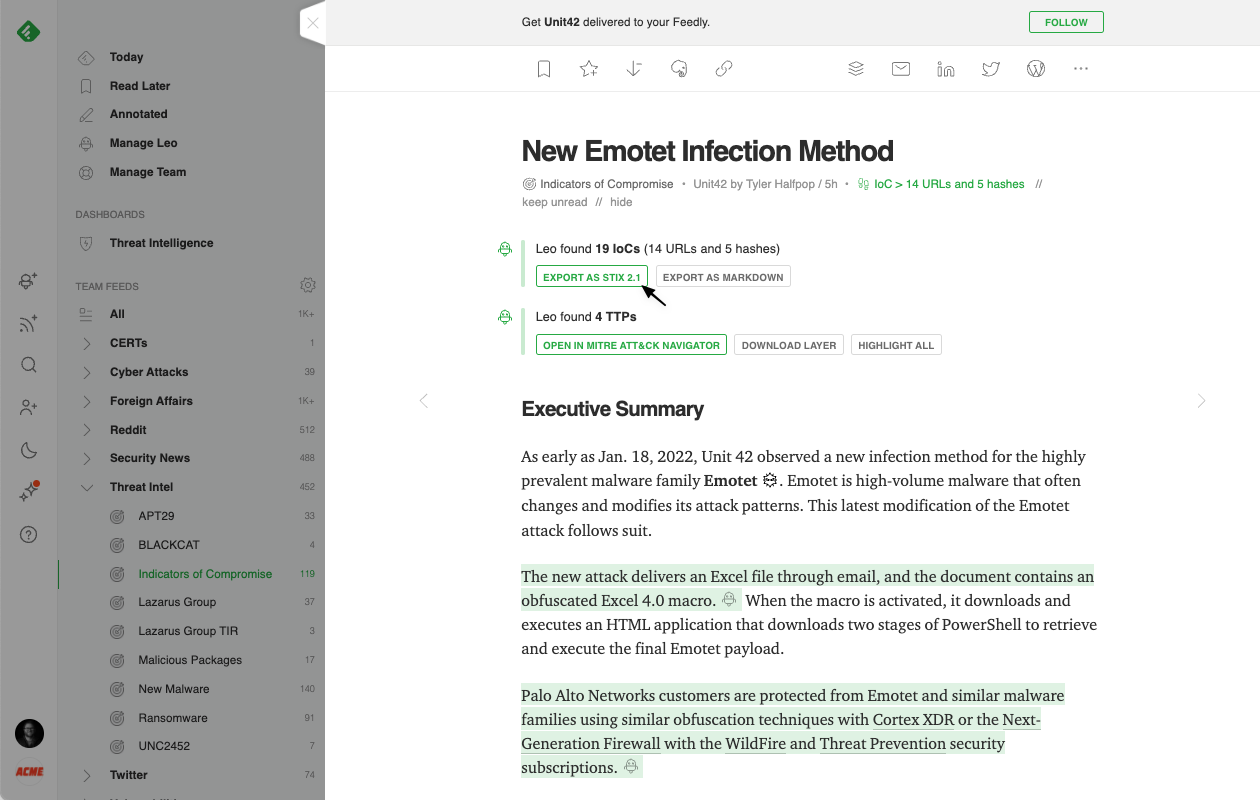
Feedly AI also automatically flags all the malicious IPs, hashes, domains, and URLs (IoCs) it identifies in articles so that they can easily be exported with links to threat actors, malware families, and vulnerabilities using STIX 2.1 and imported into Threat Intelligence Platforms (TIP).
Track cyber attacks
Security teams can efficiently track cyber attacks targeting their industry or supply chain. Feedly AI has been pre-trained to understand the concept of a cyber attack and who the target of the attack is. Here is an example of how a cybersecurity professional might ask Feedly AI to track all the cyber attacks targeted at the finance industry.
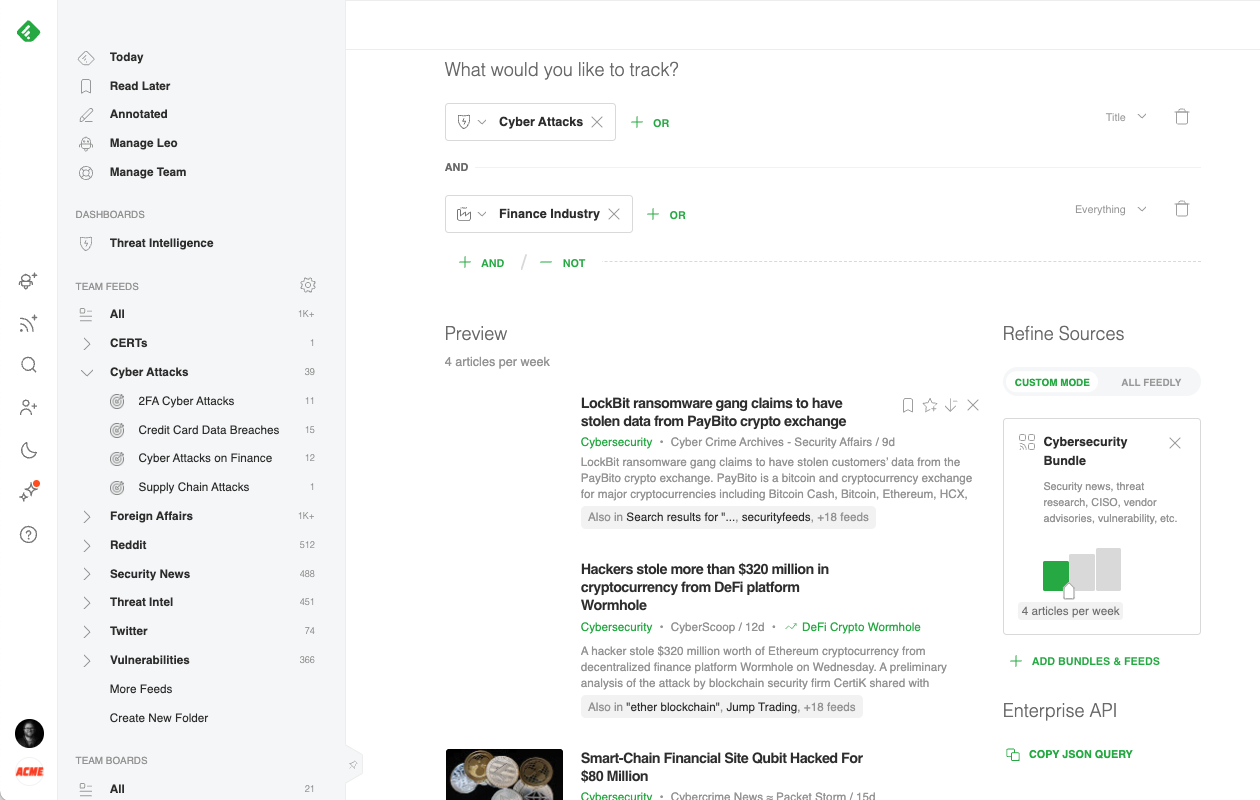
The focus can also be narrowed down to more specific threats like “data breaches impacting credit cards” or “cyber attacks using multi-factor authentication”
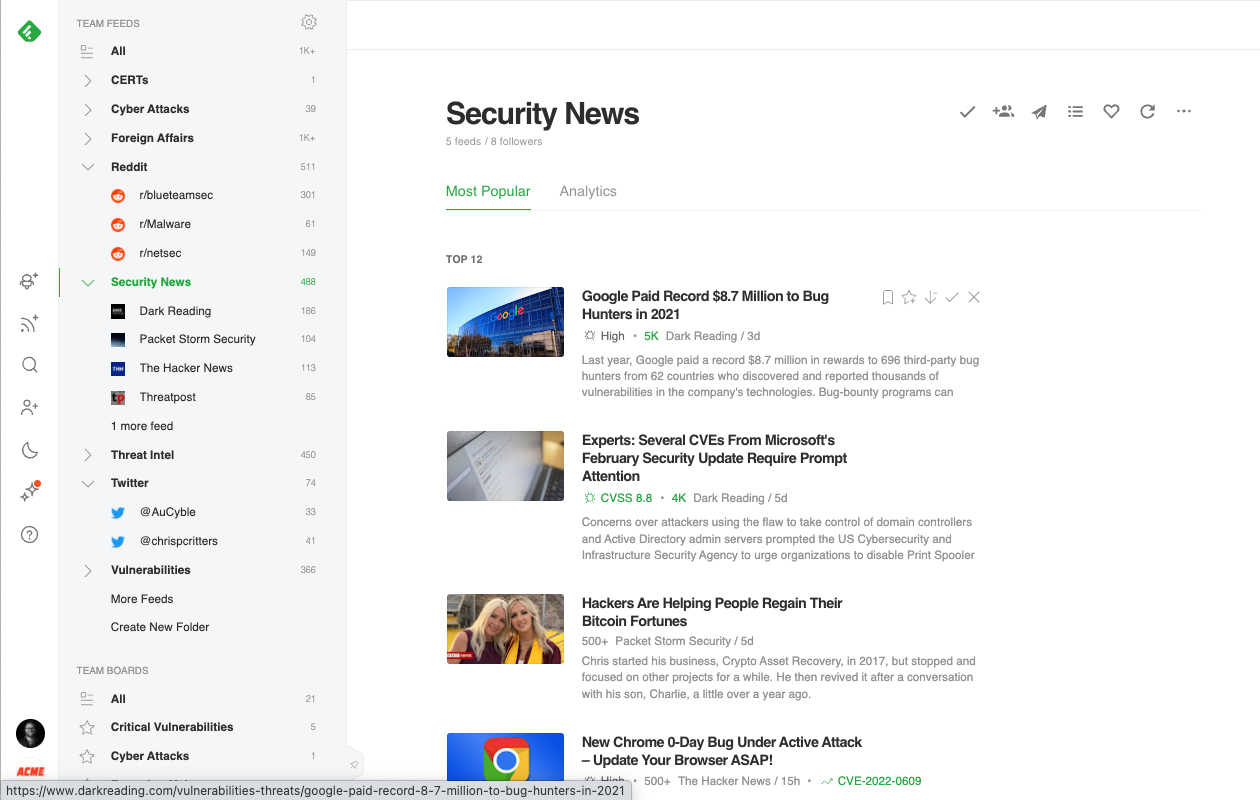
Follow trusted security feeds
Feedly allows cybersecurity teams to follow a wide variety of trusted feeds all in one place, including websites and blogs, newsletters, Reddit communities, and Twitter accounts, searches, and hashtags. The teams that get the most out of Feedly turn it into their one-stop intelligence center so they can share common sources in one place. They end up saving hours each week because they’re no longer sharing articles ad-hoc across email, Slack, and other messaging platforms.
Collect and share threat intelligence with Boards
When an article of importance surfaces, Feedly provides the tools to annotate, highlight, add notes, and save the article to a Board for review later. When an article is saved to a Team Board, Feedly for Threat Intelligence users have additional options to auto-generate Newsletters, share with Slack or Microsoft Teams, or use Feedly’s Rest API to integrate into an existing workflow.
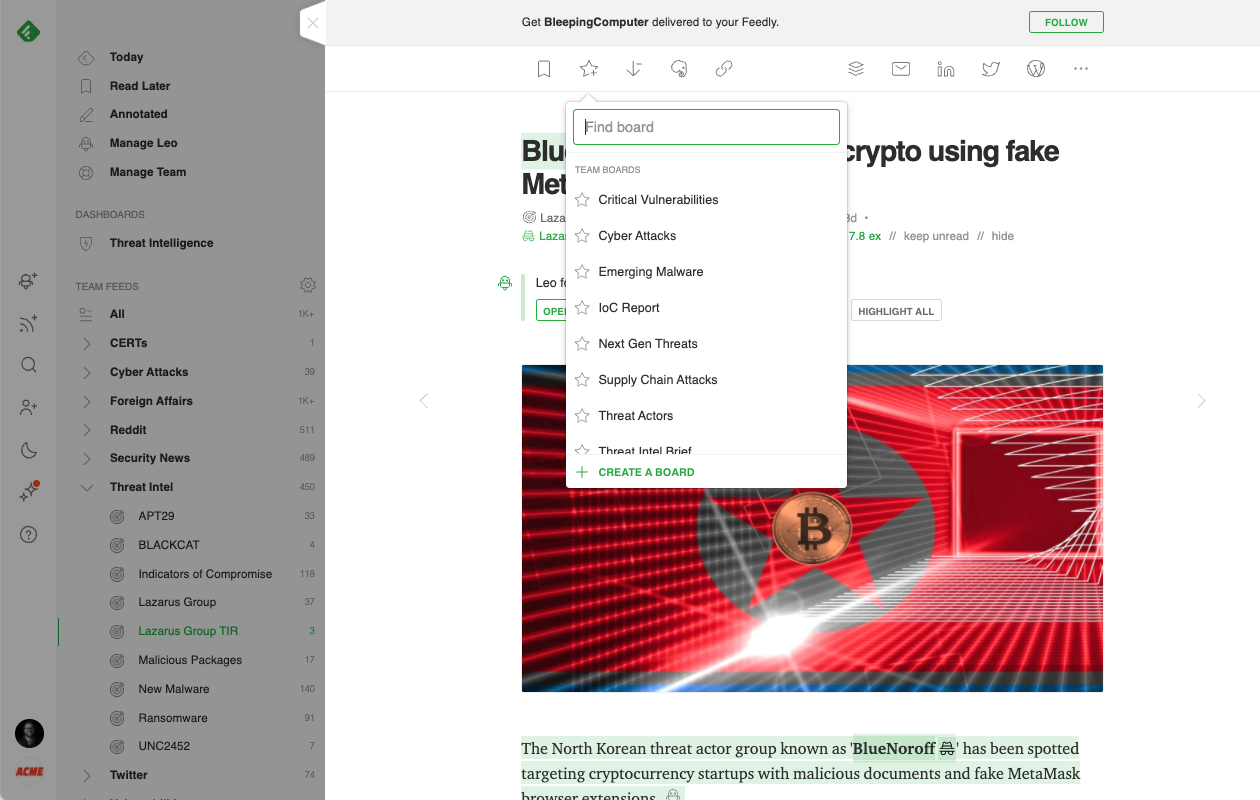
Here are a few examples of Team Boards that have helped cybersecurity teams stay organized:
- Critical Vulnerabilities Board: Save articles about exploitable vulnerabilities and zero-days that a cybersecurity team will want to research and patch as soon as possible.
- IoC Report Board: Save articles referencing IoCs that should be pushed to a threat intelligence platform.
- Threat Intelligence Brief Board: Save articles to share with an executive team.
- Threat Actors Board: Save articles describing behaviors of specific threat actors active in the industry that should be imported into the TIP for the rest of the team to research.
- Emerging Malware Board: Save articles about techniques used by emerging malware families.
- Supply Chain Attacks Board: Save instances of attacks and data breaches reference supply chain or third-party partners.
Try Feedly for Threat Intelligence
All of these features, plus many more, are available as a part of Feedly for Threat Intelligence. To learn more about any of these features, or start a free 30-day trial, click the link below.